
Both TLS and SSL are protocols that help you securely authenticate and transport data on the Internet. But what’s the difference between TLS vs SSL? And is it something you need to worry about?
In this article, you’ll learn the key differences between TLS vs SSL, as well as how both protocols connect to HTTPS. You’ll also learn why, as an end-user, you probably don’t need to worry too much about TLS vs SSL or whether you’re using an “SSL certificate” or a “TLS certificate”.
You can click below to jump to a specific section or read through the entire article:
What Is the Difference Between TLS and SSL?
TLS, short for Transport Layer Security, and SSL, short for Secure Socket Layers, are both cryptographic protocols that encrypt data and authenticate a connection when moving data on the Internet.
For example, if you’re processing credit card payments on your website, TLS and SSL can help you securely process that data so that malicious actors can’t get their hands on it.
So what’s the difference between TLS vs SSL?
Well, TLS is actually just a more recent version of SSL. It fixes some security vulnerabilities in the earlier SSL protocols.
Before you learn more about the specifics, it’s important to understand the basic history of SSL and TLS.
SSL 2.0 was first released in February 1995 (SSL 1.0 was never publicly released because of security flaws). Although SSL 2.0 was publicly released, it also contained security flaws and was quickly replaced by SSL 3.0 in 1996.
Then, in 1999, the first version of TLS (1.0) was released as an upgrade to SSL 3.0. Since then, there have been three more TLS releases, with the most recent release being TLS 1.3 in August 2018.
At this point, both public SSL releases have been deprecated and have known security vulnerabilities (more on this later).
Here’s the full history of SSL and TLS releases:
- SSL 1.0 – never publicly released due to security issues.
- SSL 2.0 – released in 1995. Deprecated in 2011. Has known security issues.
- SSL 3.0 – released in 1996. Deprecated in 2015. Has known security issues.
- TLS 1.0 – released in 1999 as an upgrade to SSL 3.0. Planned deprecation in 2020.
- TLS 1.1 – released in 2006. Planned deprecation in 2020.
- TLS 1.2 – released in 2008.
- TLS 1.3 – released in 2018.
How Do TLS and SSL Work to Secure Data?
Here’s the high-level process for how both SSL and TLS work.
When you install an SSL/TLS certificate on your web server (often just called an “SSL certificate), it includes a public key and a private key that authenticate your server and let your server encrypt and decrypt data.
When a visitor goes to your site, their web browser will look for your site’s SSL/TLS certificate. Then, the browser will perform a “handshake” to check the validity of your certificate and authenticate your server. If the SSL certificate is not valid, your users may be faced with the “your connection is not private” error, which could cause them to leave your website.
Once a visitor’s browser determines that your certificate is valid and authenticates your server, it essentially creates an encrypted link between it and your server to securely transport data.
This is also where HTTPS comes in (HTTPS stands for “HTTP over SSL/TLS”).
HTTP, and the more recent HTTP/2, are application protocols that play an essential role in transferring information over the Internet.
With plain HTTP, that information is vulnerable to attacks. But when you use HTTP over SSL or TLS (HTTPS), you encrypt and authenticate that data during transport, which makes it secure.
This is why you can safely process credit card details over HTTPS but not over HTTP, and also why Google Chrome is pushing so hard for HTTPS adoption.
Why Is It Called an SSL Certificate If SSL Is Deprecated?
Above, you learned that TLS is the more recent version of SSL and that both public releases of SSL have been deprecated for multiple years and contain known security vulnerabilities.
That might have you wondering: why is it called an SSL certificate and not a TLS certificate? After all, TLS is the modern, security protocol.
For example, if you look on the Kinsta features page, you’ll see that Kinsta advertises a free SSL certificate, not a free TLS certificate.
Don’t worry: Kinsta is not using outdated technology!
No, the reason why most people still refer to them as SSL certificates is basically a branding issue. Most major certificate providers still refer to certificates as SSL certificates, which is why the naming convention persists.
In reality, all the “SSL Certificates” that you see advertised are really SSL/TLS Certificates (that includes the free SSL certificates that we offer as part of our Cloudflare integration).
That is, you can use both the SSL and TLS protocols with your certificate.
There’s no such thing as just an SSL certificate or just a TLS certificate, and you don’t need to worry about replacing your SSL certificate with a TLS certificate.
Should You Use TLS or SSL? Is TLS Replacing SSL?
Yes, TLS is replacing SSL. And yes, you should use TLS instead of SSL.
As you learned above, both public releases of SSL are deprecated in large part because of known security vulnerabilities in them. As such, SSL is not a fully secure protocol in 2019 and beyond.
TLS, the more modern version of SSL, is secure. What’s more, recent versions of TLS also offer performance benefits and other improvements.
Not only is TLS more secure and performant, most modern web browsers no longer support SSL 2.0 and SSL 3.0. For example, Google Chrome stopped supporting SSL 3.0 all the way back in 2014, and most major browsers are planning to stop supporting TLS 1.0 and TLS 1.1 in 2020.
In fact, Google started showing ERR_SSL_OBSOLETE_VERSION warning notifications in Chrome.
So how do you make sure that you’re using the most recent versions of TLS and not older, insecure SSL protocols?
First, remember that your certificate is not the same as the protocol that your server uses. You do not need to change your certificate to use TLS. Even though it might be branded as an “SSL certificate”, your certificate already supports both the SSL and TLS protocols.
Instead, you control which protocol your website uses at a server level.
If you’re hosting at Kinsta, Kinsta already enables TLS 1.3 for you, which is the most modern, secure, and performant version, as well as TLS 1.2.
If you’re hosting elsewhere, you can use the SSL Labs tool to check which protocols are enabled for your site.
For example, if you test a website hosted at Kinsta, you can see how Kinsta enables TLS 1.2, and TLS 1.3 but disables the older, insecure versions of SSL:
 How to test which SSL/TLS protocols your server uses.
How to test which SSL/TLS protocols your server uses.
If you find that your server still supports the deprecated SSL protocols, you can reach out to your host’s support for help or follow these instructions to disable SSL on the two most popular web servers (Apache and Nginx):
Why Does Kinsta Enable Multiple TLS Protocols?
If TLS 1.3 is the most modern, performant protocol, why does Kinsta bother also enabling the slightly older TLS 1.2 protocol?
In other words: what’s the benefit of having multiple protocols enabled?
As you learned above, there are two parts to the SSL/TLS handshake:
- Your webserver
- The client (usually a visitor’s web browser)
In order for the handshake to work, both need to support the same protocol.
So the main benefit of having multiple protocols is compatibility.
For example, while Chrome and Firefox added support for TLS 1.3 almost immediately after its release in 2018, Apple and Microsoft took a little longer to add TLS 1.3 support.
Even in 2019, the following browsers still lack TLS 1.3 support:
- Internet Explorer
- Opera Mini
- Android Browser
- Opera Mobile
- UC Browser for Android
- Samsung Internet
- Baidu Browser
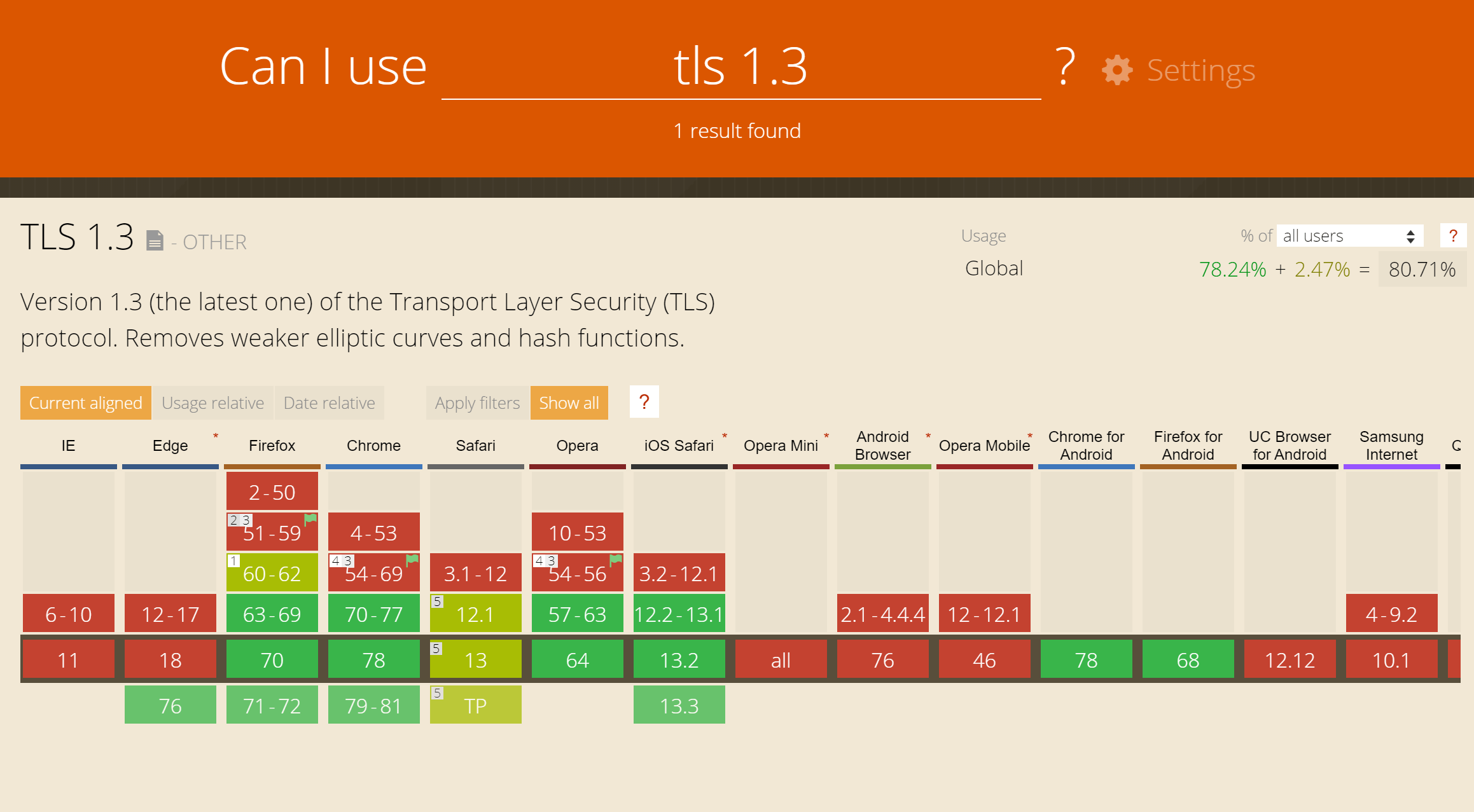 TLS 1.3 web browser support
TLS 1.3 web browser support
But while TLS 1.3 still doesn’t have full adoption, all major browsers support TLS 1.2 in 2019:
 TLS 1.2 web browser support
TLS 1.2 web browser support
By having both TLS 1.3 and TLS 1.2 enabled on your server, you can ensure compatibility no matter what, while still getting the benefits of TLS 1.3 for browsers that support it, like Chrome and Firefox.
If you want to check which SSL/TLS version your web browser is using, you can use the How’s My SSL tool:
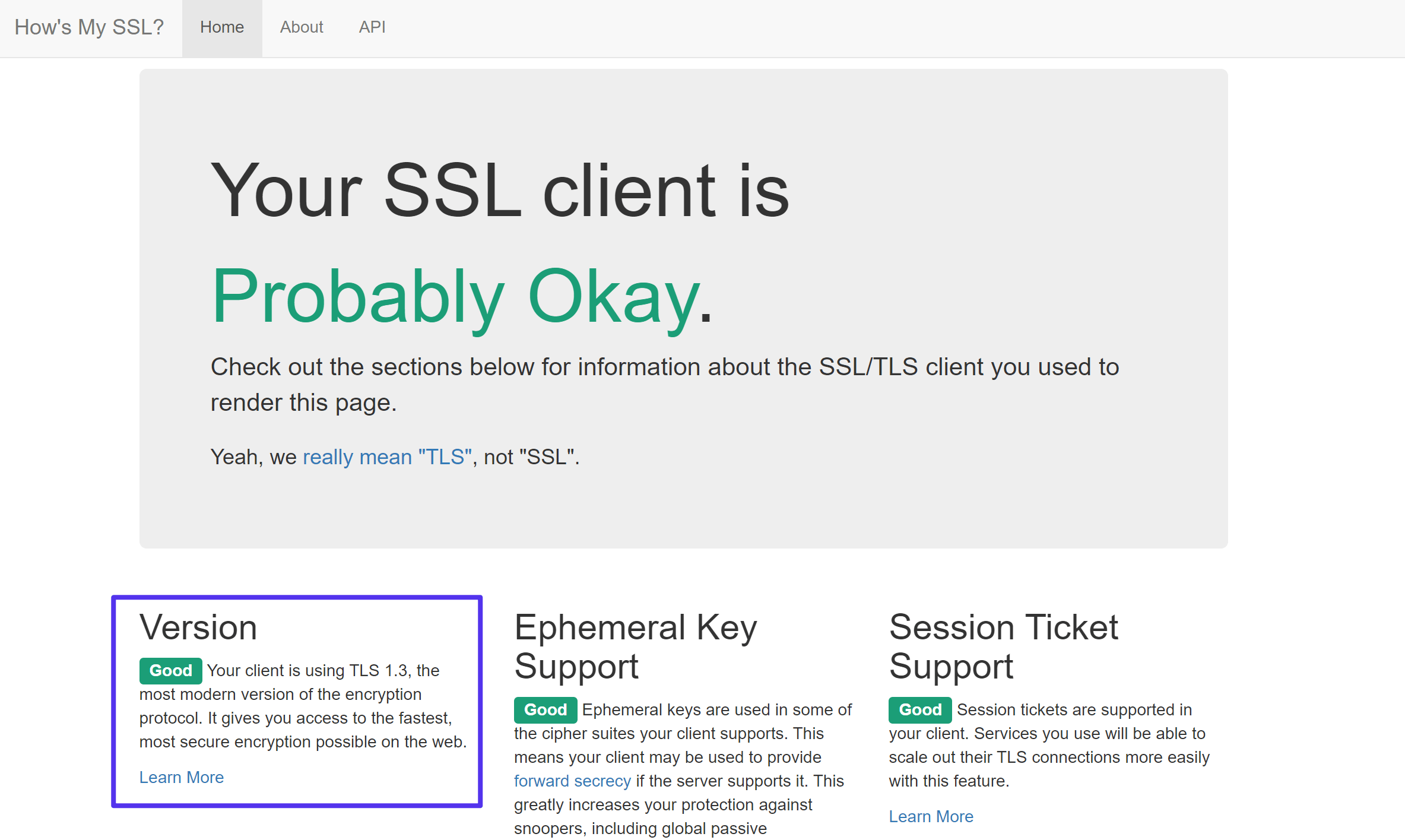 How to test which SSL/TLS protocols your browser uses
How to test which SSL/TLS protocols your browser uses
Summary
To sum everything up, TLS and SSL are both protocols to authenticate and encrypt the transfer of data on the Internet.
The two are tightly linked and TLS is really just the more modern, secure version of SSL.
While SSL is still the dominant term on the Internet, most people really mean TLS when they say SSL, because both public versions of SSL are not secure and have long since been deprecated.
To use both the SSL and TLS protocols, you need to install a certificate on your server (here’s how to install an SSL certificate on WooCommerce). Again, while most people refer to these as “SSL certificates”, these certificates support both the SSL and TLS protocols.
You do not need to worry about “changing” your SSL certificate into a TLS certificate. If you’ve already installed an “SSL certificate”, you can be confident that it also supports TLS.
It’s important to use the latest versions of TLS because SSL is no longer secure, but your certificate does not determine the protocol that your server uses. Instead, once you have a certificate, you can choose which protocols to use at a server level.
If you’re hosting at Kinsta, Kinsta currently enables TLS 1.2 and TLS 1.3, all of which are secure and supported by all major browsers.
Power your site with Kinsta’s Managed WordPress hosting, crafted for speed, security, and simplicity. With Kinsta, you get:
- Effortless control in the MyKinsta dashboard
- Unlimited free migrations, handled by our expert migrations team
- 24/7/365 support from WordPress experts
- Google Cloud’s premium infrastructure
- Enterprise-grade security through Cloudflare integration
- Global reach with 37 data centers
Enjoy your first month free!

